Security Risk: Critical
Exploitation level: Very Easy/Remote
DREAD Score: 9/10
Vulnerability: Password bypass / Privilege Escalation
Patched Version: 2.0.9.2
During a routine audit of our Website Firewall (WAF), we found a critical vulnerability affecting the popular MainWP Child WordPress plugin. According to worpdress.org, it is installed on more than 90,000 WordPress sites as as remote administration tool. We contacted the MainWP team last week and they patched the vulnerability in version 2.0.9.2 last Friday.
Per the developers request, following guidance provided in our Note to Developers, we delayed our disclosure to allow users time to update.
What are the risks?
This vulnerability allows anyone to login as an administrator only by knowing the target user’s handle (password bypass). It is very simple to exploit and a big deal as security tools like WPScan already automate the process of grabbing a list of usernames from WordPress sites.
Clients using our Website Firewall are already protected against this issue.
Technical details
*Due to the severity we will not provide a Proof of Concept and will be very light on the technical details. Make sure to update asap!
Unfortunately, this vulnerability is easy to exploit. It uses WordPress the “init” hook to trigger MainWP’s remote control mechanism.
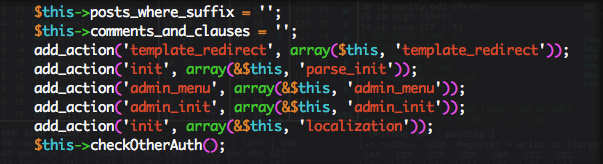
Inside this function (executed by “init”), we found the authentication check wasn’t sufficient as it allows anyone to trigger the plugin’s user login mechanism, thus making it possible for an attacker to take over any administrator account.
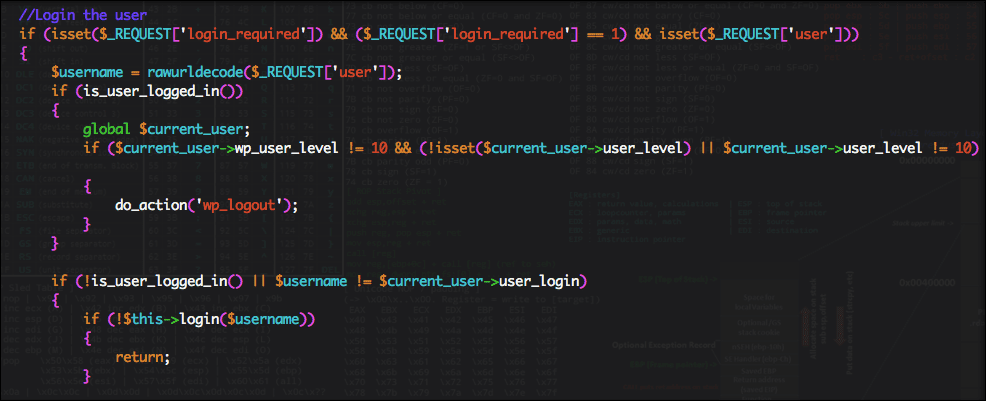
As an administrator user, the attacker is able to take full control of the website.
Update as soon as possible!
Again, if you’re using a vulnerable version of this plugin, update as soon as possible! In the event where you can not do this, we strongly recommend leveraging our Website Firewall to get it patched virtually.