Security Risk: Dangerous
Exploitation level: Very Easy/Remote
DREAD Score: 8/10
Vulnerability: Persistent XSS
Patched Version: 1.4.4
During a routine audit for our Website Firewall (WAF), we discovered a dangerous Persistent XSS vulnerability affecting the very popular WP-Super-Cache plugin (more than a million active installs according to wordpress.org). The security issue, as well as another bug-fix that was included in the issue’s original patch, are fixed in version 1.4.4.
What are the risks?
Using this vulnerability, an attacker using a carefully crafted query could insert malicious scripts to the plugin’s cached file listing page. As this page requires a valid nonce in order to be displayed, a successful exploitation would require the site’s administrator to have a look at that particular section, manually.
When executed, the injected scripts could be used to perform a lot of other things like adding a new administrator account to the site, injecting backdoors by using WordPress theme edition tools, etc.
Technical details
The issue lies in the way WP-Super-Cache would display information stored in cache file’s key, which is used by the plugin to decide what cache file must be loaded.
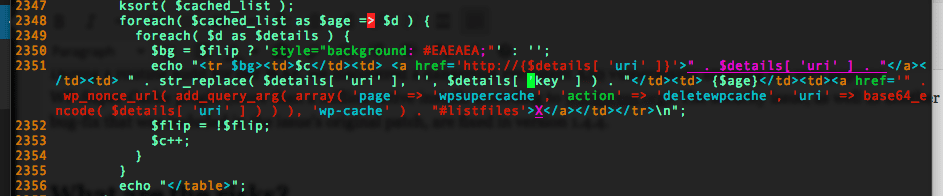
As you can see from the above, the $details[ ‘key’ ] is directly appended to the page’s content, without being sanitized first ($details[ ‘uri’ ] is sanitized somewhere else, before this snippet).
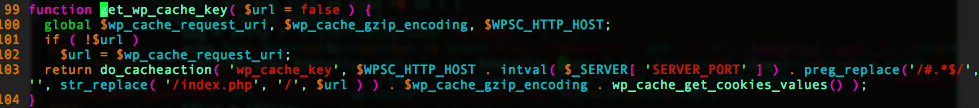
As the ‘key’ index of the $details variable contains the get_wp_cache_key() function’s return (which contains data coming straight from the user’s cookies), an attacker can insert malicious scripts on the page.