Security Advisory – High Severity– WordPress Download Manager
Advisory for: WordPress Download Manager
Security Risk: Very High
Exploitation level: Easy/Remote
DREAD Score: 9/10
Vulnerability: Code Execution / Remote File Inclusion
Risk Version: <2.7.4
If you’re using the popular WP Download Manager plugin (around 850,000 downloads), you should update right away. During a routine audit for our Website Firewall (WAF), we found a dangerous remote code execution (RCE) and remote file inclusion (RFI) vulnerability. A malicious user can exploit this vulnerability to take control of your website by uploading backdoors and modifying user passwords.
The vulnerability was discovered and disclosed last week and immediately patched by the WP Download Manager. They have released a patch in version 2.7.5 to fix this issue.
What are the risks?
Any WordPress based website running the WP Download Manager version would be susceptible to remote code execution. Allowing an attacker to inject a backdoor and change important credentials, like admin accounts.
If you use an affected version of this plugin, please update it as soon as possible! Clients on our Website Firewall have been protected from this vulnerability via our Zero Day response mechanism.
Technical details
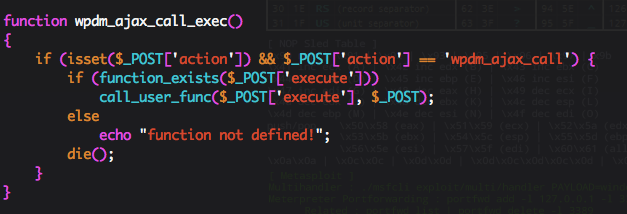
The plugin used a custom method to handle certain types of Ajax requests which could be abused by an attacker to call arbitrary functions within the application’s context. There were no permission checks before handling these special Ajax calls. This allowed a malicious individual (with a minimal knowledge of WordPress internals) to inject a backdoor on the remote site or to change the administrator’s password if the name of his account was known. As this function is hooked to the “wp” hook (which is executed every single time somebody visits a post/page), it could be abused by anyone.
The culprit
The culprit was in the wpdm_ajax_call_exec() function. It is calling a user function provided by the super global variable $_POST[‘execute’], allowing a user to call any function available within the current execution context.
Finding an interesting function to use
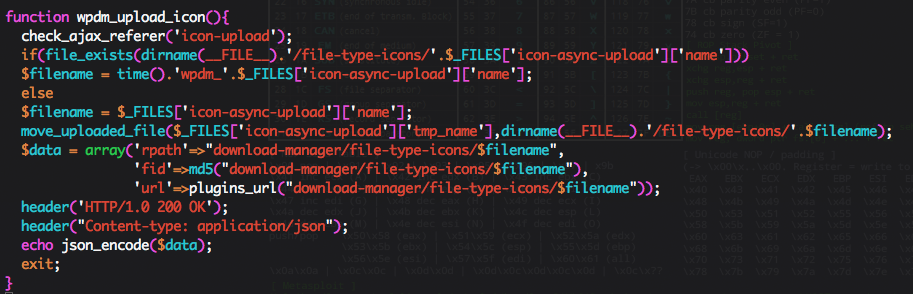
In our research for a useful function to call, we found this one really interesting. The wpdm_upload_icon() function allowed us to upload any files we want to the /file-type-icons/ directory.
The check_ajax_referer(‘icon-upload’) call that occurs before any sensitive actions is taken. This would normally prevent anyone without a valid nonce to execute it. That said, as we could execute any function in the application’s context, nothing prevented us from calling the snippet of code generating that particular nonce first.
The Result
To exploit this issue, an attacker would need to generate a valid nonce, and then send a request that calls the wpdm_upload_icons() function to upload his backdoor on it’s target.
Once this done, he might do just about anything he wants with it.