
Tell me if this sounds familiar: any connection from inside the corporate network is trusted and any connection from the outside is not. This is the security strategy used by most enterprises today. The problem is that once the firewall, or gateway, or VPN server creating this perimeter is breached, the attacker gets immediate, easy and trusted access to everything.
 CC BY-SA 2.0 image by William Warby
CC BY-SA 2.0 image by William Warby
There’s a second problem with the traditional security perimeter model. It either requires employees to be on the corporate network (i.e. physically in the office) or using a VPN, which slows down work because every page load makes extra round trips to the VPN server. After all this hassle, users on the VPN are still highly susceptible to phishing, man-in-the-middle and SQL injection attacks.
A few years ago, Google pioneered a solution for their own employees called BeyondCorp. Instead of keeping their internal applications on the intranet, they made them accessible on the internet. There became no concept of in or outside the network. The network wasn’t some fortified citadel, everything was on the internet, and no connections were trusted. Everyone had to prove they are who they say they are.
Cloudflare’s mission has always been to democratize the tools of the internet giants. Today we are launching Cloudflare Access: a perimeter-less access control solution for cloud and on-premise applications. It’s like BeyondCorp, but you don’t have to be a Google employee to use it.
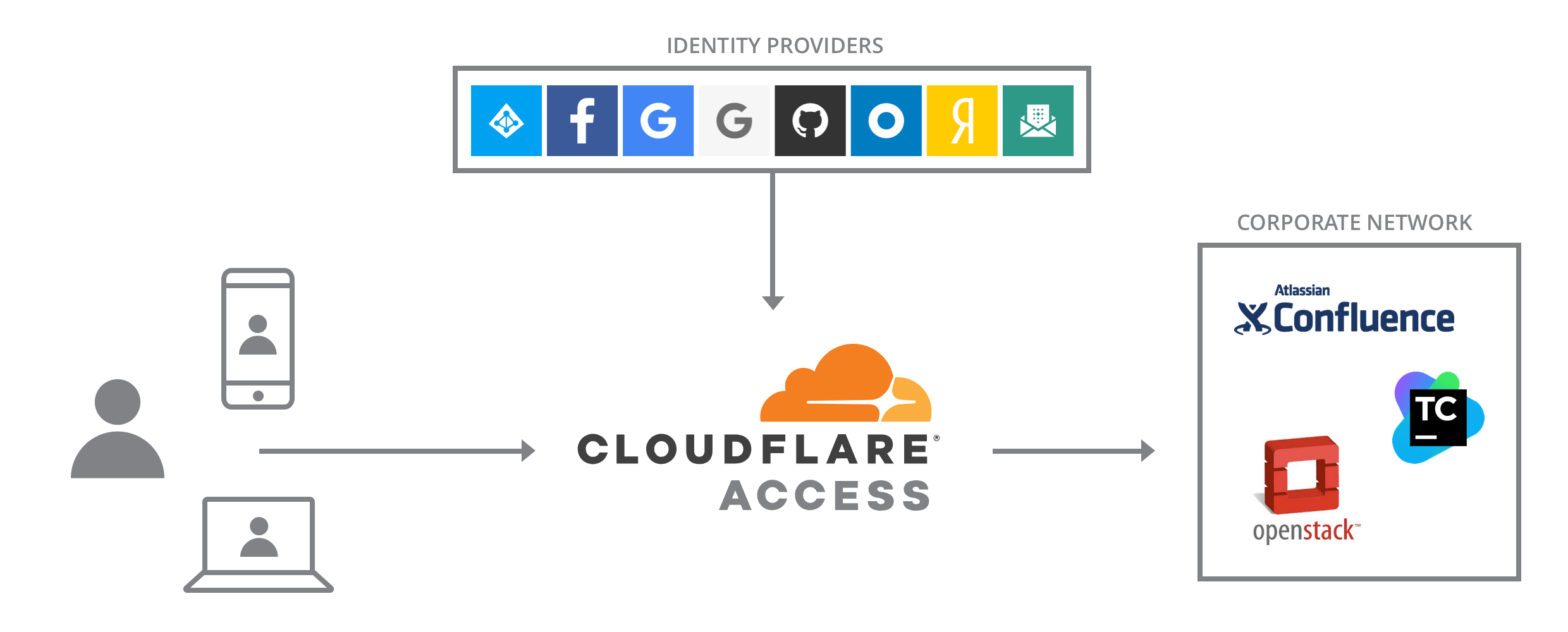
How does Cloudflare Access work ?
Access acts as an unified reverse proxy to enforce access control by making sure every request is:
Authenticated: Access integrates out of the box with most of the major identity providers like Google, Azure Active Directory and Okta meaning you can quickly connect your existing identity provider to Cloudflare and use the groups and users already created to gate access to your web applications. You can additionally use TLS with Client Authentication and limit connections only to devices with a unique client certificate. Cloudflare will ensure the connecting device has a valid client certificate signed by the corporate CA, then Cloudflare will authenticate user credentials to grant access to an internal application.
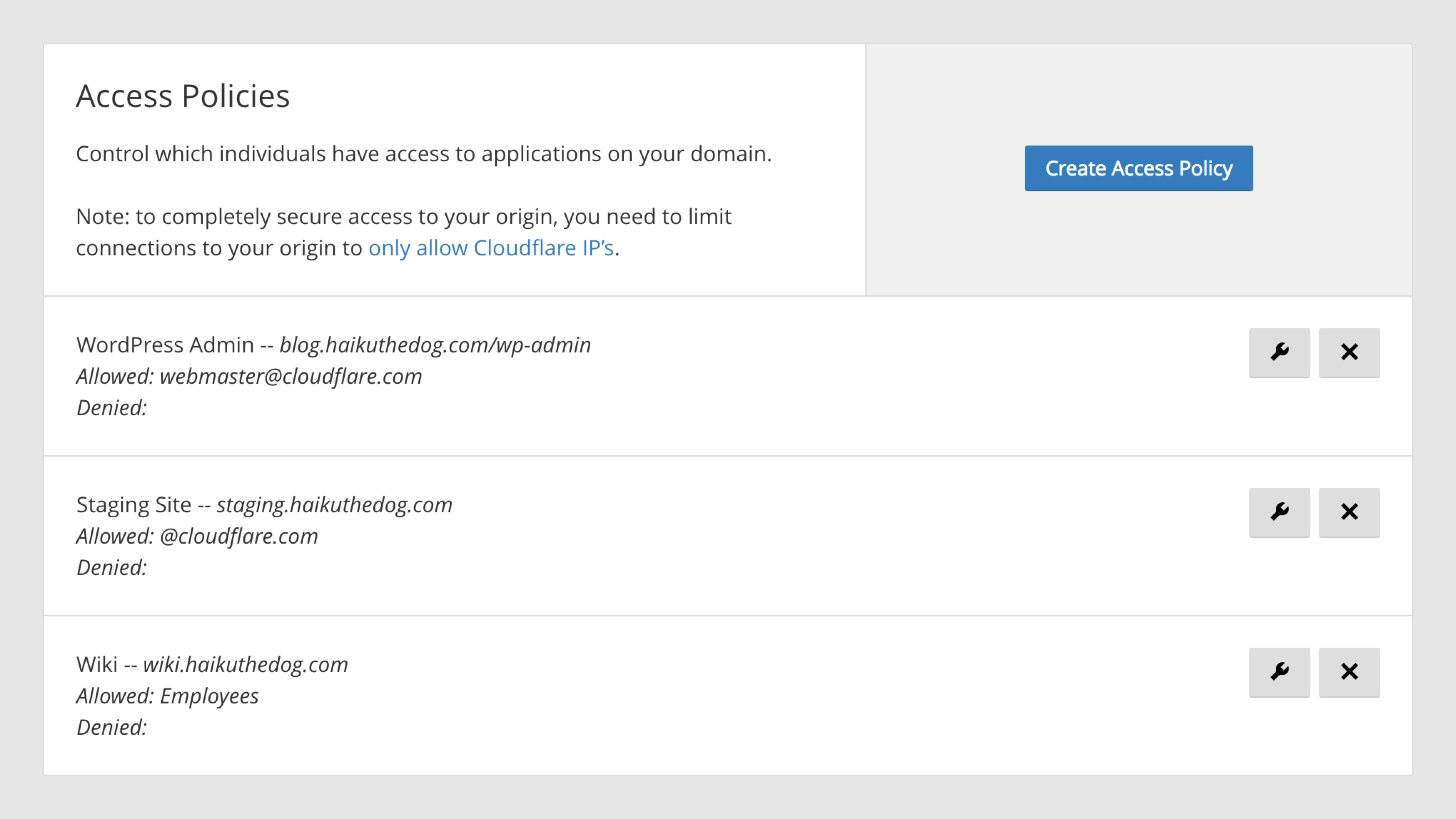
Authorized: The solution lets you easily protect application resources by configuring access policies for groups and individual users that you already created with your identity providers. For example, you could ensure with Access that only your company employees can get to your internal kanban board, or lock down the wp-admin of your wordpress site.
Encrypted: As Cloudflare makes all connections secure with HTTPS there is no need for a VPN.
To all the IT administrators who’ve been chastised by a globetrotting executive about how slow the VPN makes the Internet, Access is the perfect solution. It enables you to control and monitor access to applications by providing the following features via the dashboard and APIs:
- Easily change access policies
- Modify session durations
- Revoke existing user sessions
- Centralized logging for audit and change logs
Want an even faster connection to replace your VPN? Try pairing Access with Argo. If you want to use Access in front of an internal application but don’t want to open up that application to the whole internet, you can combine Access with Warp. Warp will make Cloudflare your application’s internet connection so you don’t even need a public IP. If you want to use Access in front of a legacy application and protect that application from unpatched vulnerabilities in legacy software, you can just click to enable the Web Application Firewall and Cloudflare will inspect packets and block those with exploits.
Cloudflare Access allows employees to connect to corporate applications from any device, any place and on any kind of network. Access is powered by Cloudflare’s global network of 120+ data centers offering adequate redundancy and DDoS protection and proximity to wherever your employees or corporate office might be.
Get Started:
Access takes 5-10 minutes to setup and is free to try for up to one user (beyond that it’s $3 per seat per month, and you can contact sales for bulk discounts). Cloudflare Access is fully available for our enterprise customers today and in open beta for our Free, Pro and Business plan customers. To get started, go to the Access tab of the Cloudflare dashboard.